A Wake-Up Call: When Unauthorized Access Threatens Operations
Cloud security isn’t just a technical need in today’s digital world; it’s also a business must. Companies use Amazon Web Services (AWS) to run their businesses, but if they don’t have good Identity and Access Management (IAM), they could lose assets, have security problems, or not follow the rules.
Someone tried to access an organization’s AWS system using stolen credentials without permission. Lack of strong security measures could have caused data loss, business interruptions, or financial harm.
Fortunately, AWS IAM was in place, utilizing multi-factor authentication (MFA), role-based access control, and stringent IAM policies. The threat was neutralized before any harm was done.
Effective cloud security is a foundational requirement for long-term growth and trust. This experience drives a vital lesson for all businesses.
Why is AWS IAM Essential for Business Security and Compliance?
Organizations often overlook the critical nature of cloud security until faced with a costly incident. AWS IAM enables secure access control, empowering businesses to manage users, enforce security policies, and protect sensitive data.
📌 Key Benefits of AWS IAM for Businesses:
✅ Regulatory Compliance: Ensures adherence to GDPR, PCI-DSS, SOC 2, and ISO 27001 standards.
✅ Financial Protection: This reduces the risk of costly data breaches, which average $4.45 million per incident (IBM 2023).
✅ Operational Continuity: Prevents unauthorized access that could disrupt operations and damage reputation.
✅ Customer & Investor Trust: Robust security builds credibility and confidence, attracting investors and retaining customers.
By using AWS IAM, businesses can secure their cloud environments, prevent cyber threats, and comply with regulations. This ensures that cloud operations run smoothly and safely.
How to Secure AWS Access with IAM?
Excessive access privileges are a common threat to cloud security. AWS IAM allows organizations to implement role-based access control, ensuring users have only the permissions they need.
📌 Business Best Practices for Secure IAM Implementation:
- Implement Role-Based Access Control (RBAC) for assigning permissions based on roles.
- Apply the Principle of Least Privilege: It states that users should only access what is required.
- Avoid using AWS root accounts for daily tasks: create IAM roles instead.
As shown in Figure 1, a user assumes an IAM role and is assigned a policy that governs access to an S3 bucket (for example, allowing listing bucket contents while denying object deletions), ensuring secure and controlled access.
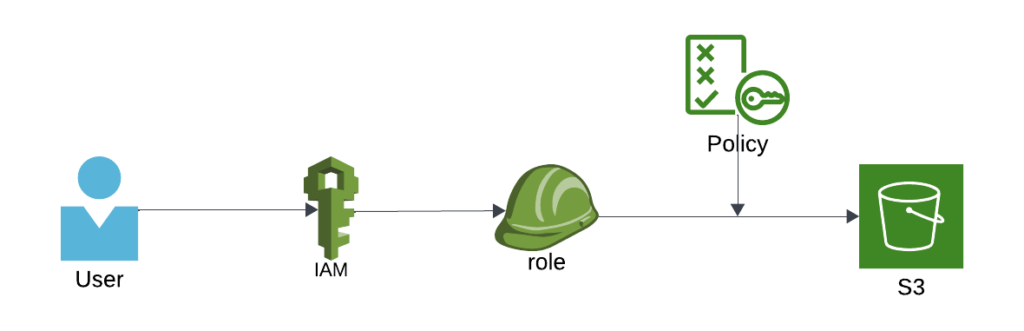
Figure 1: IAM Role-Based Access Control for S3 with Policy Enforcement
How to Implement IAM Users & Roles in AWS:
- Create IAM Users:
- Navigate to AWS IAM Console → Users → Add User.
- Assign specific permissions based on role requirements.
- Define IAM Roles for Secure Access:
- Go to IAM → Roles → Create Role.
- Select trusted AWS services (e.g., EC2, Lambda).
- Attach precise policies to control actions.
- Set Up IAM Policies to Restrict Access:
- Example JSON policy to allow listing but deny deletion in S3:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:ListBucket",
"Resource": "arn:aws:s3:::secure-data-bucket"
},
{
"Effect": "Deny",
"Action": "s3:DeleteObject",
"Resource": "arn:aws:s3:::secure-data-bucket/*"
}
]
}
Result: Users can view data but cannot delete critical files, enhancing security.
Strengthening Security with Multi-Factor Authentication (MFA)
Credential theft remains a prevalent threat. MFA (Multi-Factor Authentication) provides an additional security layer by requiring two or more verification methods.
📌 Business Best Practices for MFA Implementation:
- Enforce MFA for all IAM users, prioritizing administrators.
- Use Virtual MFA apps like Google Authenticator for standard users.
- Deploy hardware-based MFA tokens (YubiKey, RSA) for high-risk roles.
As shown in Figure 2, an IAM user signs into the AWS Management Console using their account ID, username, and password, with an additional security layer provided by Multi-Factor Authentication (MFA) to enhance access control and prevent unauthorized logins.
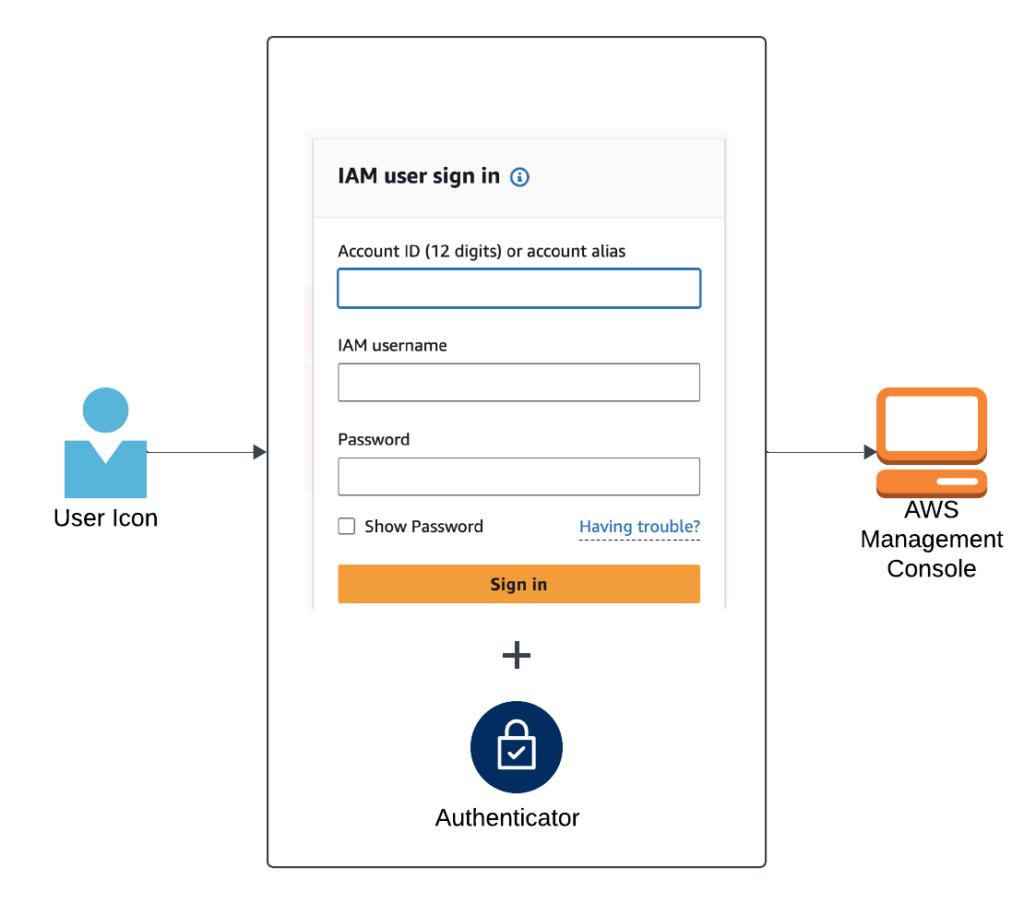
Figure 2: IAM User Login with Multi-Factor Authentication (MFA)
How to Enable MFA in AWS IAM?
- Access AWS IAM Console → Select Users.
- Click on username → Navigate to Security Credentials.
- Under Multi-Factor Authentication (MFA), click Assign MFA Device.
- Choose Virtual MFA Device, scan the QR code, and confirm codes.
Result: Prevents unauthorized access even if a password is compromised.
Centralizing AWS Access Management with AWS Organizations
For multi-account management, AWS Organizations provides centralized control, ensuring consistent IAM policies across all accounts.
📌 Business Best Practices for AWS Organizations:
- Use AWS Organizations to unify account management.
- Implement Service Control Policies (SCPs) for standardized security.
- Restrict AWS region usage to comply with data residency laws.
As shown in Figure 3, AWS Organizations allows centralized management of multiple AWS accounts by grouping them into Organizational Units (OUs) and applying Service Control Policies (SCPs) to enforce security rules, ensuring standardized access control and compliance across all accounts.
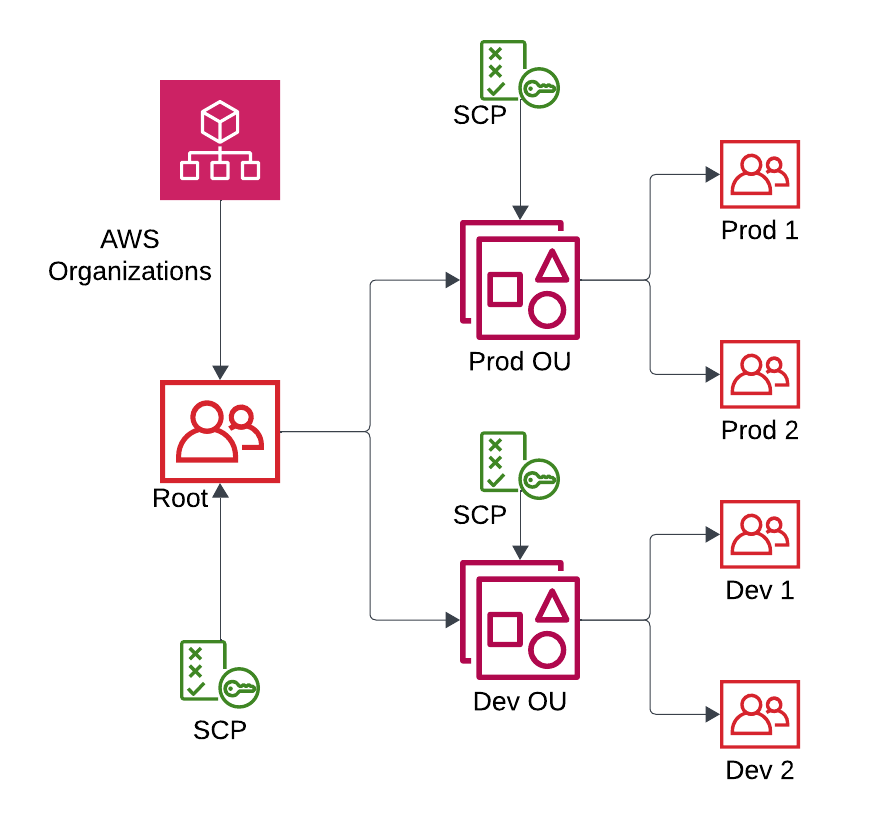
Figure 3: Centralized Access Control with SCPs in AWS Organizations
📌 How to Set Up AWS Organizations?
- Open AWS Organizations Console → Click Create Organization.
- Add multiple AWS accounts into a single organizational unit (OU).
- Apply Service Control Policies (SCPs) to enforce security rules.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Deny",
"Action": "*",
"Resource": "*",
"Condition": {
"StringNotEquals": {
"aws:RequestedRegion": ["us-east-1", "us-west-2"]
}
}
}
]
}
Result: Prevents unauthorized AWS activities outside approved regions, ensuring data security.
FAQs
1. What is AWS IAM, and why is it important?
AWS IAM (Identity and Access Management) enables businesses to control access to AWS services and resources securely, ensuring only authorized users can perform specific actions.
2. How does MFA enhance AWS security?
MFA adds an extra layer of security by requiring a second verification method, such as a mobile app code or hardware token, reducing the risk of unauthorized access.
3. Can IAM policies restrict access based on geographic location?
Yes, IAM policies and Service Control Policies (SCPs) can restrict access to AWS services based on regions or IP addresses, enhancing compliance and security.
4. What is the difference between IAM users and roles?
IAM Users are for individual accounts with specific credentials, while IAM Roles are assumed by users or services, providing temporary access with defined permissions.
5. How does AWS Organizations help in managing multiple accounts?
AWS Organizations simplifies management by allowing centralized policy enforcement, consolidated billing, and streamlined account creation, enhancing security and operational efficiency.

